Application Layer DDoS Simulator
Update(november 2010): ddosim v0.2 has been released. You can find it at: https://sourceforge.net/projects/ddosim/.
ddosim is a tool that can be used in a laboratory environment to simulate a distributed denial of service (DDOS) attack against a target server. The test will show the capacity of the server to handle application specific DDOS attacks. ddosim simulates several zombie hosts (having random IP addresses) which create full TCP connections to the target server. After completing the connection, ddosim starts the conversation with the listening application (e.g. HTTP server).
ddosim is written in C++ and runs on Linux. Its current functionalities include:
-
HTTP DDoS with valid requests
-
HTTP DDoS with invalid requests (similar to a DC++ attack)
-
SMTP DDoS
-
TCP connection flood on random port
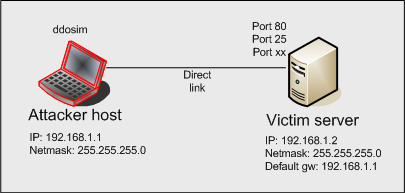
In order to simulate such an attack in a lab environment we need to setup a network like this:
On the victim machine ddosim creates full TCP connections – which are only simulated connections on the attacker side.
There are a lot of options that make the tool quite flexible:
Usage: ./ddosim
-d IP Target IP address
-p PORT Target port
[-k NET] Source IP from class C network (ex. 10.4.4.0)
[-i IFNAME] Output interface name
[-c COUNT] Number of connections to establish
[-w DELAY] Delay (in milliseconds) between SYN packets
[-r TYPE] Request to send after TCP 3-way handshake. TYPE can be HTTP_VALID or HTTP_INVALID or SMTP_EHLO
[-t NRTHREADS] Number of threads to use when sending packets (default 1)
[-n] Do not spoof source address (use local address)
[-v] Verbose mode (slower)
[-h] Print this help message
Examples:
1. Establish 10 TCP connections from random IP addresses to www server and send invalid HTTP requests (similar to a DC++ based attack):
./ddosim -d 192.168.1.2 -p 80 -c 10 -r HTTP_INVALID -i eth0
2. Establish infinite connections from source network 10.4.4.0 to SMTP server and send EHLO requests:
./ddosim -d 192.168.1.2 -p 25 -k 10.4.4.0 -c 0 -r SMTP_EHLO -i eth0
3. Establish infinite connections at higher speed to www server and make HTTP valid requests:
./ddosim -d 192.168.1.2 -p 80 -c 0 -w 0 -t 10 -r HTTP_VALID -i eth0
4. Establish infinite TCP connections (without sending a Layer 7 request) from local address to a POP3 server:
./ddosim -d 192.168.1.2 -p 110 -c 0 -i eth0
More background info:
Some of the hardest to mitigate distributed denial of service attacks are the ones targeting the application layer (in TCP/IP stack). They are difficult to stop because they look legitimate to classic firewalls which let them pass freely (for an example look here). The only way to stop this kind of attacks is deep packet inspection (layer 7 inspection) which means a lot of money/resources.
In general, a DDoS attack is performed by an armie of bots (zombies) that simultaneously send attack packets to a victim server. If we talk about UDP packets (ex. targeting a DNS server), the attack is easier to implement because a zombie needs to send a single UDP packet (multiple times) to contribute to the attack. But in case of a TCP based attack, the zombie needs first to establish the full TCP 3-way handshake and then send the data packets (e.g. HTTP GET request). ddosim successfully simulates this attack scenario.
If you have any questions regarding ddosim, please let me know.
August 14, 2009 at 2:04 pm
[…] […]
August 18, 2009 at 10:51 am
I am encountering this error whilst executing this tool on FC 3
./ddosim -d 99.99.20.65 -p 80 -c 0 -w 0 -t 10 -r HTTP_VALID -i eth1
./ddosim: error while loading shared libraries: libnet.so.0: cannot open shared object file: No such file or directory
August 18, 2009 at 7:35 pm
You should do an “export LD_PRELOAD=libnet.so” first.
November 10, 2009 at 6:44 am
Perhaps you can elaborate more on the “export LD_PRELOAD=libnet.so”. Is it a command or what? Maybe you could briefly write the step by step instructions in shell? Thank you.
November 20, 2009 at 3:29 pm
‘export LD_PRELOAD=libnet.so’ is kind of a hack. The best method is to install the ‘official’ package libnet0-dev which will provide you the correct libnet.so library.
November 6, 2010 at 12:07 am
[…] https://stormsecurity.wordpress.com/2009/03/03/application-layer-ddos-simulator/ DDoS Simulator is a tool that can be used in a laboratory environment to simulate a distributed […]
November 6, 2010 at 2:13 pm
Hello,
i cannot configure ddosim:
> configure: error: libnet0 (dev) is required for this program
but i have libnet and its headers installed:
$ rpm -qf /lib/libnet.so.0
libnet-1.1.2.1-141.1.i586
$ rpm -qf /usr/include/libnet.h
libnet-1.1.2.1-141.1.i586
libnet_1.0.2a-devel-1.0.2a-1.1.i586
my system is opensuse 11.3 – possibly that “libnet0” has another name in it. which files exactly needed for building ddosim?
or how could i make any workaround for configure to make it think libnet0 is installed?
Cheers
November 6, 2010 at 9:03 pm
Hi,
Maybe you have libnet1. It must be libnet0.
Regards,
November 6, 2010 at 9:10 pm
there is no such package in opensuse:
http://www.google.com/search?q=site:download.opensuse.org+libnet0&ie=utf-8&oe=utf-8
http://packages.opensuse-community.org/index.jsp?searchTerm=libnet0
that`s why i think it just has another name (libnet_1.0.2a maybe?).
could you please tell me exact list of files (libs, headers, etc) needed for ddosim to work?
Cheers
November 9, 2010 at 7:16 am
Hi,
I developed ddosim in Backtrack (Ubuntu 8.10 basically) and I have the following libnet packages installed:
root@bt:~# dpkg -l | grep libnet0
ii libnet0 1.0.2a-7 library for the construction and handling of network packets (obsolete)
ii libnet0-dev 1.0.2a-7 Development files for libnet0 (obsolete)
Hope this helps,
Adrian
November 8, 2010 at 11:02 am
[…] DDOSIM simula uma série de máquinas zombies com ips randômicos (o ip do host zombie muda) criando uma […]
November 9, 2010 at 8:48 pm
[…] […]
November 11, 2010 at 4:02 pm
Ubuntu 10.10
configure: error: libnet0 (dev) is required for this program.
I have libnet1-dev installed, installing libnet0-dev(downloaded deb) conflicts. Also I need to keep libnet1-dev on my system. How to install ddosim now?
Thanks
November 12, 2010 at 10:53 am
Hi,
Libnet0-dev is required for ddosim to work. Maybe it would be a good approach to install it in a (Debian based) virtual machine.
Regards,
Adrian
November 15, 2010 at 9:21 am
Oh boy, this is great tool, I will surely going to try it out 🙂
November 15, 2010 at 6:28 pm
Please share your results with us.
November 16, 2010 at 2:47 pm
Can I compile with another version of libnet?
November 16, 2010 at 9:55 pm
Sorry, I’m afraid you cannot do that with the current version of ddosim. You need libnet0.
Try apt-get install libnet0-dev.
November 19, 2010 at 10:55 am
[…] More Info : 1) DDOSIM at Sourceforge 2) Application Layer DDoS Simulator […]
December 8, 2010 at 8:09 am
Great tool. Is there any tools for windows?
Break The security
December 8, 2010 at 9:20 pm
Thanks. I do not know a (free) similar tool for Windows… If anyone knows, please share.
December 22, 2010 at 12:12 pm
[…] More Info : 1) DDOSIM at Sourceforge 2) Application Layer DDoS Simulator […]
December 22, 2010 at 6:58 pm
Installing in Ubuntu 10.10
Install required packages:
sudo apt-get install build-essential
sudo apt-get install libpcap-dev
wget http://mirrors.us.kernel.org/ubuntu//pool/universe/libn/libnet0/libnet0_1.0.2a-7_amd64.deb
sudo dpkg -i libnet0_1.0.2a-7_amd64.deb
wget http://mirrors.us.kernel.org/ubuntu//pool/universe/libn/libnet0/libnet0-dev_1.0.2a-7_amd64.deb
sudo dpkg -i libnet0-dev_1.0.2a-7_amd64.deb
wget http://downloads.sourceforge.net/project/ddosim/ddosim-0.2.tar.gz
tar xfv ddosim-0.2.tar.gz
cd ddosim-0.2/
./configure
make
sudo make install
It should be updated to use libnet1 instead. then you could just say
sudo apt-get install libnet1-dev
December 23, 2010 at 2:32 pm
Thanks for posting these steps.
However, the libnet0 package should not conflict with a previously existing libnet1.
The system that I used for building and testing the application was a 32 bit machine with Backtrack (Ubuntu 8.10) and libnet0-dev.
July 26, 2011 at 10:08 am
nice tutorial
works well in my BT5_x86
December 24, 2010 at 6:07 am
This is really an awesome tool, wish it could run out of lab environment to test application in real time environment, anyways thanks for addition.
December 24, 2010 at 7:48 am
Running DDOSIM out of lab is not really possible because it simulates distributed (multiple source IPs) attacks using a connection-orented protocol (TCP) which needs at least the 3way handshake before sending any useful data.
So the communication must be bidirectional. The packets (TCP SYN-ACK) sent by the server must reach the attacker (having random IP address).
I do not think the simulation of a distributed DOS on a connection oriented protocol is possible outside lab environment.
If anyone has other ideas, please share.
December 27, 2010 at 7:02 am
so if we put the ip address of the victim server outside the lab like 221.223.224.225 on port 80, will it work then?
December 27, 2010 at 9:20 am
No, it will NOT work. Simply because the packets sent by the target server will never reach the attacker (to complete the 3way handshake).
December 27, 2010 at 10:07 am
So do you have any alternative for that?
December 29, 2010 at 9:56 pm
Nope. Don’t think there is one…
February 17, 2011 at 4:06 am
How to include application level attacks in payload? I tried editing ddosim.cpp and compiling it, but it says
In file included from ddosim.h:9,
from ddosim.cpp:7:
/usr/include/libnet.h:87:2: error: #error “byte order has not been specified, you’ll”
In file included from ddosim.h:9,
from ddosim.cpp:7:
/usr/include/libnet.h:88: error: expected unqualified-id before string constant
How to change the code to include payload?
February 18, 2011 at 12:42 pm
What you can easily do right now is to modify the current payloads in senderThread.cpp and recompile ddosim.
Custom payloads is a feature planned for the next release.
March 17, 2011 at 4:22 am
The payload is declared as u_char *… it takes only 4 bytes…i changed the type to char * in tcputils.cpp , tcputils.h , senderthread.cpp….it throws an error…how to include payload of greater size ?
March 12, 2011 at 6:25 am
Hi,
I’m doing a research on DoS and I wonder if this tool could help establish DoS case. I have the following questions:
1) can I run it on a single machine not connected to LAN (in other words, Does the machine that runs the DDosim has to be connected physically to other machine?)
2) suppose I run the tool, can I collect the results in order to graph them??
3) Can I modify the code to get a specific scenario?
Your response through this is highly appreciated
Best Regards,
Moe
March 12, 2011 at 11:15 am
Hi Moe,
1. Yes, if your target server is on a virtual machine hosted on the same physical machine. Running ddosim against yourself (on localhost) I do not think is possible.
2. No, in this version of ddosim you cannot collect the results. You have just the statistics displayed periodically (number of connections established, reset, finished). Maybe in a future version I will implement the collection feature, thanks for suggestion.
3. Yes, you can modify the code to do whatever you want it to do.
Cheers,
Adrian
May 17, 2011 at 5:47 pm
With help from the previous comments I was able to compile on CentOS 5. Make gives me an error:
ddosim.cpp: In function ‘int main(int, char**)’:
ddosim.cpp:58: error: ‘libnet_host_lookup’ was not declared in this scope
ddosim.cpp:184: error: ‘libnet_host_lookup’ was not declared in this scope
ddosim.cpp: In function ‘u_long getLocalIp(const std::string&, std::string&)’:
ddosim.cpp:292: error: ‘libnet_open_link_interface’ was not declared in this scope
ddosim.cpp:296: error: ‘libnet_get_ipaddr’ was not declared in this scope
ddosim.cpp: In function ‘u_long resolveNameToIp(char*, std::string&)’:
ddosim.cpp:316: error: ‘libnet_name_resolve’ was not declared in this scope
ddosim.cpp:317: error: ‘LIBNET_ERR_FATAL’ was not declared in this scope
ddosim.cpp:317: error: ‘libnet_error’ was not declared in this scope
make: *** [ddosim.o] Error 1
Anybody can help me?
Thank you.
May 18, 2011 at 6:38 am
You most probably do not have the development package for libnet0 installed.
August 16, 2011 at 9:34 am
Hi, thanks for writing a tool like this. However, I was wondering if you can use it against a host over the internet with the -n option (no spoofing). I tested it (against a machine under my control), but no ack is sent after synack is received and therefore the tool ends up performing a syn flood. Could you please comment on this? Many thanks.
August 19, 2011 at 7:43 am
Hi, I tested this scenario and it works. Make sure you have connectivity / correct routing set.
To create 10 connections to the target host without spoofing the source address you should use the following command:
./ddosim -d http://www.your_host.com -p 80 -i eth0 -c 10 -r HTTP_VALID -n -v
You should receive a final status like this:
Final results:
TCP connections: 10 SYN_SENT, 10 ESTABLISHED, 0 RST, 0 FIN_WAIT_1
Cheers,
December 24, 2011 at 4:54 pm
please help me to configur and run ddosim on centos 5
Thank you
December 26, 2011 at 9:21 am
Hi,
I did not test ddosim on other Linux distributions. If you have the necessary libraries, it should compile and work smoothly.
Cheers,
February 28, 2012 at 11:29 am
I have a network environment that’s pretty much similar to what’s described here above except that the packets ddosim goes thro’ a switch to the server. All I’m seeing is SYNs
TCP connections: 180300 SYN_SENT, 0 ESTABLISHED, 0 RST, 0 FIN_WAIT_1. 6040
and wireshark says:
Acknowledgement Number: Broken TCP. The acknowledgement field is nonzero while the ACK flag is not set.
Not sure what’s going on.. Has anyone seen this behavior?
February 28, 2012 at 11:34 am
One thing I missed noting at ‘February 28, 2012 at 11:29 am’:
I tested with HTTP_VALID, HTTP_INVALID and the plain TCP connection flood (as shown in the example in the article above). They all appear to show the same behavior.
Any clues appreciated.
February 28, 2012 at 2:32 pm
(continuation from February 28, 2012 at 11:34 am):
Upon further investigation, I saw ddosim indeed sends non-zero ACKs when TCP ACK flag is not set. However, the TCP connections complete when the host running ddosim and the victim server are connected directly (as suggested by the author).
It’s the device standing in between the hosts in my setup, that’s dropping the requests because of invalid ACK number.
It would be nice to nice to see the problem fixed, if it’s easy.
February 28, 2012 at 6:54 pm
Since the TCP connections complete when the host running ddosim and the victim server are connected directly, it means that the network device that is standing between attacker and victim is modifying the packets somehow.
You can make a simple test – try to establish a single connection using ddosim – and check that all the packets sent from attacker reach the victim and vice versa.
March 9, 2012 at 1:50 pm
Geeks,
I am still not able to figure out how to recover from the set back of libnet0-dev on centos. Any help would be greatly appreciated.
Regards
March 9, 2012 at 2:41 pm
As I already said, I did not test ddosim on CentOS. DDosim was built and tested on a Backtrack machine (Debian based) having the package libnet0-dev installed.
April 2, 2012 at 3:15 pm
Hi ,
My tool works. Now I have question if I use application DDoS attack could You tell me how often and how many http reguest are send to victim? Can we manage number of request or type of request?
For example we can setup how many connection TCP we can setup and how many user we can simulate but for example when we do application DDOS then we do not need many connection and many users but many request. Can we setup this parameter?
best regards,
Sebastian
April 4, 2012 at 10:27 am
Hi Sebastian,
I’m glad you made it work 🙂
The current version of ddosim does not report the number of requests/second sent to victim server. However, the parameter -w specifies the delay between packets. You can adjust it in order to obtain an efficient packet rate.
I’m afraid that multiple requests per user are not possible in the current architecture of ddosim. Right now you have a distinct user making a single HTTP request. I’ll think about this for the next release.
Cheers,
Adrian
April 4, 2012 at 2:18 pm
Hi Adrian,
When will You think release new version Your software?
I am very interesting this tool. Do You know mabe other tool which I can use?
BR,
Sebastian
December 8, 2013 at 6:47 am
Sir I have a question regarding the HTTP GET flood creation. Does DDOSIM creates HTTP GET flood or does it create SYN flood since when i simulated DDOSIM in my computer, there was no complete 3-way handshake because i could see only SYN and SYN+ACK but no ACK. Please reply. Thanks in advance.
December 8, 2013 at 1:31 pm
DDOSIM can do HTTP GET flood. In order for this to happen, the SYN-ACK packet must reach back the attacker machine. This happens if: (1) option -n is used or (2) the victim machine must be configured such that it send ALL packets to the attacker machine (ex. attacker is victim’s default gateway).
December 10, 2013 at 5:25 pm
I have used -n option but it shows the ip address of the attacker. I wanted a HTTP GET flood using random ip addresses and to create a complete 3-wau handshake.